How do attacks happen?
Suffering an attack on your website might be a daunting experience, as your data might be lost or stolen or held for ransom by the attackers. If you have a hacked website, it is easy to panic. In such situations, you must remain calm and assess the incident objectively.
As a website owner, you must exercise caution and take all security measures to keep your website safe.
If you do not have a backup, then a full recovery of a hacked website might become time-consuming and expensive.
Security professionals are in high demand due to ever-increasing attacks on web applications.
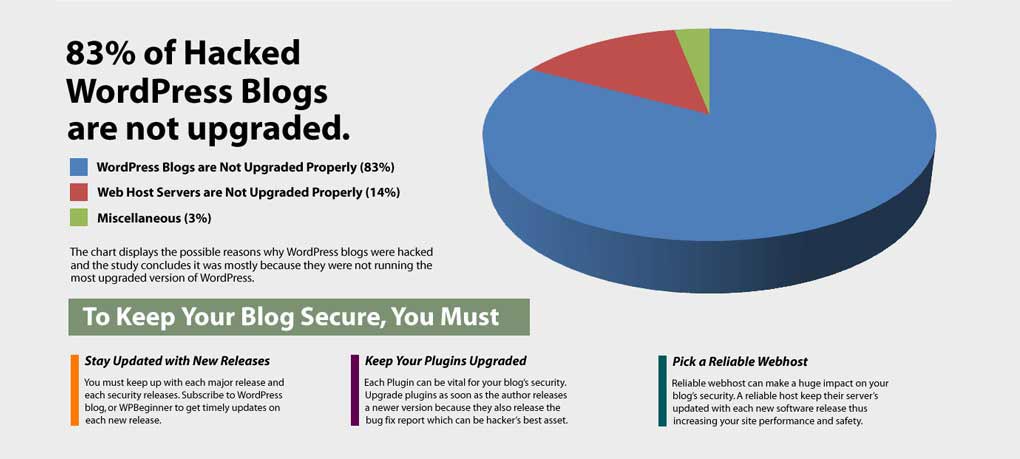
Web developers need to follow stringent security practices, updating their software to the newest version, encompassing all recent patches.
SOURCE: neilpatel.com
SQL injections and Cross Site Scripting
Two of the most common attack methods are SQL injections and Cross Site Scripting.
Through SQL injections, the attacker can insert SQL metacharacters into input fields (where users submit data), to manipulate SQL queries.
You can manipulate SQL queries from a given parameter, and gain unauthorized information from the database.
Attackers can also destroy the database and cause considerable damage, including monetary. SQL injection is the top OWASP (The Open Web Application Security Project) application security risk.
Cross Site Scripting (XSS) is when a malicious javascript is embedded in an input field without validation, such as comment section on the site. If the field is incorrectly configured, the javascript will then execute when anyone visits the site and load that particular comment.
Ransomware is a type of malware that encrypts your data and asks for a payment in order to decrypt your data.
Instructions are sent to the owner of the website, with payment usually demanded in bitcoin or some other online currency.
Ransomware virus enters through a malicious email attachment, or due to the absence of a critical security patch.
You may try to find the decryption key for the ransomware on nomoreransom.org and recover your files, but generally, the keys aren’t always available.
If no key is available, you only have two options. Pay the ransom and hope that you get the keys to decrypt your files.
This is generally not recommended because you might not get the keys, and by paying, you keep making ransomware profitable.
With the recent value spike of cryptocurrencies, it has become increasingly common for attackers to exploit compromised systems to mine cryptocurrencies.
A hacked website might then include javascript that load when a visitor visits the site, and mine cryptocurrencies in the background.
This can be detected by noticing how a seemingly simple site drains a significant amount of computing resources from the client machine.

SOURCE: cloudways.com
Third on the list of OWASP application security risk is sensitive data exposure.
Some web applications are not able to protect sensitive information such as credit card data, personal identifying data relating to financial and healthcare and so on, very well.
Extra precautions must be exercised whenever sensitive information is interacting with the browser.
Security misconfiguration is the sixth application security risk, encompassing insufficient security configurations (eg. weak username and password, not having password protection), open cloud storage and error messages that disclose sensitive information.
Signs of a hacked website
Logging is vital in order to detect if a website has been compromised.
Most attacks will only leave traces in the logs if sufficient logging is enabled. Typically you will have to dig and run queries on your logs in order to detect different attacks.
For instance, an SQL attack could be visible in the logs as a large data transfer, since they gained unauthorized access to the whole database.
Some of the valuable data that attackers may desire to have is a complete list of usernames and passwords, credit card information and other sensitive or personal identifying information.
E-commerce websites are typical targets for gaining access to credit card information.
Look for an activity that deviates from normal behaviors, such as abnormally large data transfers, repeated failed queries or connections over non-standard ports (https and https go over 80 and 443 normally for instance).
What to do after website gets hacked?
It is very imperative that you should not panic, after realizing that your website has been compromised.
Your first action might be that of panic and disbelief, but you must get over the initial thoughts and get to work.
You must access the damage caused by the attackers, and note down all the information you can find at that moment (time, suspicious activity, database queries etc.).
This will help you figure out the type of attack and how it took place.
Damages of cyber attacks are of varying seriousness, hence the actions to mitigate these attacks are diverse.
An SQL injection attack that exfiltrated the credit card information of all the customers requires a completely different response from an XSS attack that mine cryptocurrencies in the background on the visitor’s machine.
Creating a timeline of all the information you can gather right after realizing there has been a breach is important.
This will let you map out when the attack happened and how long the system was compromised.
The website and local environment should be scanned for malware by various anti-virus scanners.
A backup of the hacked website can be taken in order to later investigate the malware and it’s origin while the new site is put up and running.
A complete list of activities to perform if you think you have been hacked is mentioned here.
If the attacker has gained access to the login credentials from the database, then your users will also need to create new passwords as there will be a thorough and password reset.
You as the owner might also have to change all your passwords and make strong randomized ones for each service.
A password manager is a good solution to generate and store strong unique passwords for the various services.
You must also consult with your hosting provider about the hacking incident.
Affected users must also be notified, and the situation must be explained in detail to all victims.
Depending on the severity of the attack, you might consider involving the authorities.
